Setting up SSL for Tomcat and SIA in 6 Minutes
Setting up security on your BusinessObjects servers can be a daunting task. So... below is a script and a set of instructions that should have you up and running in 6 minutes (if you read quickly).
I’m Using
The Fast Version
If you trust me, know a bit about security, and have your own backed-up server to try this out on, skip down to the section “The Script” and follow the steps from there.
Don’t be Confused
There’s a lot of different terms and overlapping topics around security. To clarify a few things, there are two different concepts in this post.
Part 1: User-to-Tomcat
Setting up Tomcat to accept communication over HTTPS. This affects users connecting the the CMC of BI Launch Pad in their browsers. By using HTTPS, data sent between a user’s computer and the server will be encrypted. This encrypted communication is called SSL (you can correct people and call it TLS, but let’s call it SSL). Note that since we’re using a certificate we created ourselves, users will be told that the certificate is not trusted by their browser. In production environments, a certificate should be obtained from a Certificate Authority.
Part 2: Tomcat-to-BusinessObjects Servers
This isn’t seen by the users. It’s about configuring Tomcat to encrypt its communications with the SIA, which then handles communications to the other servers (CMS, FRS, APS, etc.) using SSL. In many scenarios, tomcat will be running on the same actual server as the SIA, so this might be overkill. But if you’ve put an instance of Tomcat out in a DMZ, you will probably want it to encrypt communications with the SIA.
CMA
First of all, be nervous about running scripts you find on the internet. It’s your server, not mine, and I accept no responsibility if something goes wrong. If you’re a consultant, walk through each line of the script with your client’s security guru before running it, you can refer back to the manual to explain to them what each line does.
If you’re not using BI4, check each line of the script against the administrator manual for your version, particularly the file paths.
With that out of the way, this script is fairly harmless, it doesn’t delete or move any files (only create and copy), and doesn’t do any configuration of BusinessObjects, these are manual steps at the end of the post.
The Script
To be fair, start your stopwatch now.
The scripts below will generate keystores, certificates and keys and move them to a common folder where the SIA and Tomcat can access them.
This has created some files, but not configured BusinessObjects in any way. There are three tasks remaining.
Configure Tomcat to Communicate With a User’s Browser Over HTTPS
A .keystore file will have been created in C:\SSL by the above script. All you need to do is refer to this file in Tomcat’s configuration file.
Configure Tomcat to use the SSL Certificates for Communication With the SIA
Configure the SIA to Use the SSL Certificates
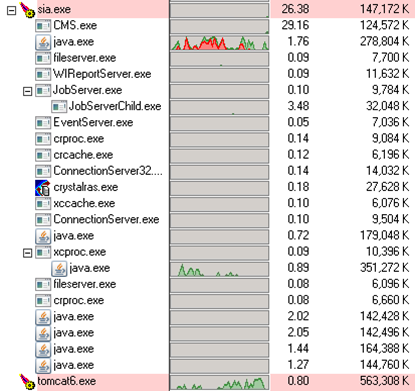
It helps here to have task manager open, since if one of the files is wrong, you will see the SIA start, then maybe the CMS, then you will see them end. If this happens, use Windows Event Viewer to troubleshoot and check every step above.
Bonus Tip: You really should be using task manager’s big brother Process Explorer, which shows processes as a hierarchy.
So, you’re done! Hopefully this helps you out if you're doing this for the first time, and gives you something to re-use whenever you need to set up security.
- See more at: http://blog.davidg.com.au/2012/12/setting-up-ssl-for-tomcat-and-sia-in-6.html#sthash.nIv6kNni.dpufI’m Using
- BI Platform BI4.0 SP5
- Windows Server 2008R2
- The below script has been tested on multiple 2008R2/BI4 servers, but not other versions.
- You have RDP/console access to your BusinessObjects server as an administrator
- You are familiar with BusinessObjects (e.g. know what the SIA is, know what Tomcat is for)
- You don’t know a thing about SSL
- The administrator manual: Securing BI Platform > Configuring Servers for SSL
- SAP Note 1648573 (configuring Tomcat to use SSL over https)
- SAP Note 1642329 (configuring the backend servers for SSL. This largely resembles the administrator manual, but is for 3.1)
The Fast Version
If you trust me, know a bit about security, and have your own backed-up server to try this out on, skip down to the section “The Script” and follow the steps from there.
Don’t be Confused
There’s a lot of different terms and overlapping topics around security. To clarify a few things, there are two different concepts in this post.
Part 1: User-to-Tomcat
Setting up Tomcat to accept communication over HTTPS. This affects users connecting the the CMC of BI Launch Pad in their browsers. By using HTTPS, data sent between a user’s computer and the server will be encrypted. This encrypted communication is called SSL (you can correct people and call it TLS, but let’s call it SSL). Note that since we’re using a certificate we created ourselves, users will be told that the certificate is not trusted by their browser. In production environments, a certificate should be obtained from a Certificate Authority.
Part 2: Tomcat-to-BusinessObjects Servers
This isn’t seen by the users. It’s about configuring Tomcat to encrypt its communications with the SIA, which then handles communications to the other servers (CMS, FRS, APS, etc.) using SSL. In many scenarios, tomcat will be running on the same actual server as the SIA, so this might be overkill. But if you’ve put an instance of Tomcat out in a DMZ, you will probably want it to encrypt communications with the SIA.
CMA
First of all, be nervous about running scripts you find on the internet. It’s your server, not mine, and I accept no responsibility if something goes wrong. If you’re a consultant, walk through each line of the script with your client’s security guru before running it, you can refer back to the manual to explain to them what each line does.
If you’re not using BI4, check each line of the script against the administrator manual for your version, particularly the file paths.
With that out of the way, this script is fairly harmless, it doesn’t delete or move any files (only create and copy), and doesn’t do any configuration of BusinessObjects, these are manual steps at the end of the post.
The Script
To be fair, start your stopwatch now.
The scripts below will generate keystores, certificates and keys and move them to a common folder where the SIA and Tomcat can access them.
- On your server’s desktop, create a blank text file.
- Rename the file to SSL Setup.cmd, you will be warned about changing a file’s extension.
- Right click the file and click Edit, which will open it in Notepad.
- Copy the below text into the file:
REM Create the Keystore for web clients to connect to Tomcat - Save and close the file.
- Double-click the cmd file and it will open a command window and start asking questions. For simplicity, enter every password as Password1 even though some of these passwords don’t relate to each other. (If you want to use a different password, change it in the 5th line from the bottom in the script before running it.)
- You’ll be prompted for things like country and organizational unit as you go, you can enter whatever you like here. You’ll be prompted more than once for the same thing, this is as expected.
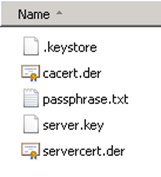
- Once finished, the command window will close automatically. You can navigate to C:\SSL and check these five files exist to confirm everything has worked.
"C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\win64_x64\jdk\bin\keytool.exe" -genkey -alias tomcat -keyalg RSA
MKDIR C:\SSL
COPY "%USERPROFILE%\.keystore" C:\SSL
REM Create the certificates for the CMS
cd "C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\win64_x64"
sslc req -config sslc.cnf -new -out cacert.req
sslc rsa -in privkey.pem -out cakey.pem
sslc x509 -in cacert.req -out cacert.pem -req -signkey cakey.pem -days 365
MKDIR demoCA
MKDIR demoCA\private
MKDIR demoCA\newcerts
COPY cacert.pem demoCA
COPY cakey.pem demoCA\private
COPY NUL index.txt
COPY index.txt demoCA
<nul (set/p z=11111111111111111111111111111111) >serial
COPY serial demoCA
sslc req -config sslc.cnf -new -out servercert.req
sslc rsa -in privkey.pem -out server.key
sslc ca -config sslc.cnf -days 365 -out servercert.pem -in servercert.req
sslc x509 -in cacert.pem -out cacert.der -outform DER
sslc x509 -in servercert.pem -out servercert.der -outform DER
<nul (set/p z=Password1) >passphrase.txt
COPY cacert.der C:\SSL
COPY servercert.der C:\SSL
COPY server.key C:\SSL
COPY passphrase.txt C:\SSL
This has created some files, but not configured BusinessObjects in any way. There are three tasks remaining.
- Configure tomcat to communicate with a user’s browser over HTTPS
- Configure Tomcat to use the SSL certificates for communication with the SIA
- Configure the SIA to use the SSL certificates
Configure Tomcat to Communicate With a User’s Browser Over HTTPS
A .keystore file will have been created in C:\SSL by the above script. All you need to do is refer to this file in Tomcat’s configuration file.
- Open the Central Configuration Manager (CCM).
- Stop Tomcat.
- Navigate to server.xml, located in C:\Program Files (x86)\SAP BusinessObjects\Tomcat6\conf
- Make a copy for a backup.
- Edit the file in Notepad, find the line beginning with <Connector port="8443"
- Uncomment this line. This means remove the <!-- at the start of the line and the --> at the end of the line.
- Add in the attributes keystorePass="Password1" keystoreFile="C:\SSL\.keystore". Change the password here if you typed in something different while the script was running. The end result should look like this.
<Connector port="8443" protocol="HTTP/1.1" SSLEnabled="true"
maxThreads="150" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS" keystorePass="Password1" keystoreFile="C:\SSL\.keystore"/> - Save and close server.xml.
Configure Tomcat to use the SSL Certificates for Communication With the SIA
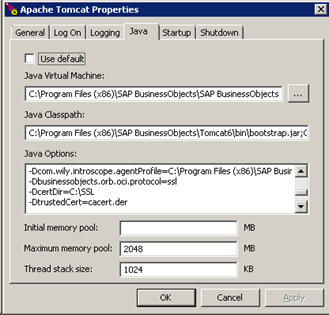
- In the start menu, locate Tomcat Configuration.
- Go to the Java tab.
- Enter in the below text right down the bottom of the Java Options section. If any of these are wrong, Tomcat won’t start, so double-check for stray characters, including spaces at the ends of the lines.
-Dbusinessobjects.orb.oci.protocol=ssl
-DcertDir=C:\SSL
-DtrustedCert=cacert.der
-DsslCert=servercert.der
-DsslKey=server.key
-Dpassphrase=passphrase.txt - Click OK.
- Start Tomcat again.
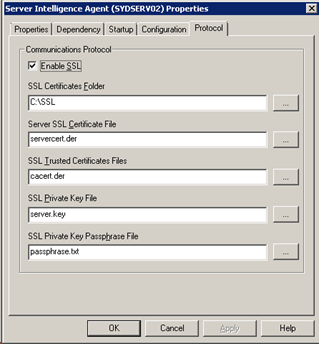
Configure the SIA to Use the SSL Certificates
- In the CCM, stop the Server Intelligence Agent.
- Double click the SIA to edit its properties.
- Go to the Protocol tab.
- Tick Enable SSL.
- Fill in each of the fields so that it looks like this.
- Click OK.
- Start the SIA.
It helps here to have task manager open, since if one of the files is wrong, you will see the SIA start, then maybe the CMS, then you will see them end. If this happens, use Windows Event Viewer to troubleshoot and check every step above.
Bonus Tip: You really should be using task manager’s big brother Process Explorer, which shows processes as a hierarchy.

So, you’re done! Hopefully this helps you out if you're doing this for the first time, and gives you something to re-use whenever you need to set up security.
Hi Haritha,
ReplyDeleteI have a question here, Can i get your email Id plz?
Regards,
Kumar
Hi Haritha,
ReplyDeleteI need your suggestion in implementing the SSL for Tomcat and SIA:
1. I am on BI 4.2 SP3 version, so i guess i can use the code?
2. I have followed this link for (https://evtechnologies.com/enforcing-https-for-secure-sap-businessobjects-bi4/) for SSL implementation but it's not working here even though i got the Certificates signed by CA. When i access Tomcat URL it says "Your connection is not private"
3. I had sent the CSR file which i generated using Microsoft MMC to my Local IT team to get it signed and in return i got 3 certificates ( Intermediate, Root & ServerCerticiate) .CRT files from them. so not sure how i can use them in tomcat and SIA configurations as i dont have ( “servercert.der” and “cacert.der”) which was suggested here.
Any help here?
Regards,
Kumar
SIA is stopping after enabling it to SSL as per above steps. Logs are not helpful as well. Can you suggest any key points please ?
ReplyDeleteNice Post very usable....
ReplyDeleteYou should put a disclaimer with this post:
ReplyDelete**This is the "quick and dirty" method and should only be used for dev (if that) environments. It technically enables SSL, but does not use a trusted CA, and users will receive errors every time they visit the site.